This is an issue that pops up occasionally when you have firewalls and dynamic IP addresses. The firewalls allow your IP though for security (blocking all other conections), but then your IP changes and you are denied access to your database.
The development environment I am currently using is one where I develop on an Amazon EC2 instance. To fetch data, my software on the EC2 server connects to a shared Amazon RDS (MYSQL database instance) which other developers use as well.
To manage the database, I connect directly to the RDS instance with a database client, in this case Navicat, which is particularly good.
So...when my home office IP changes, I have no access to the database until the firewall is updated with the new IP address.
This happened to me earlier this week, and usually I ask the project manager to make the update, and after that, all is well. This time, I offered to change how I do it, and to route my Navicat traffic via my EC2 instance to be freed from the hassle in the future. In this case, the EC2 instance has port 22 and port 80 open to everyone, so a changing IP won't be an issue there...
Here is the synopsis:
Navicat --- ( ssh port 22 ) ---> EC2 ( 127.0.0.1:3306 ) ---> RDS ( port 3306 )
Initially, I thought I would turn to the hacker and pentester friend, Netcat....known as the swiss army knife of networking.
I did manage to set up a backpipe that routed the MYSQL traffic, but it did not solve the issue entirely. It failed to stay connected. Recently I managed to trigger a rare behaviour from MYSQL where it denies me access to the database after ten or more bad connection attempts, so I did want to avoid that hassle too.
Here is how netcat could route the traffic, assuming you have set up the backpipe already:
/bin/nc -k -l 3306 0<pipes/navicat_to_rds_pipe | nc dev-rds.xxxxxxxxx.us-east-1.rds.amazonaws.com 3306 1>pipes/navicat_to_rds_pipe
The working solution though was to use rinetd to do the re-routing. Heres how to do it:
EC2 Instance
This is a bitnami provisioned linux (ubuntu) AWS EC2 box, so your linux commands may be different. These commands are executed as root on the server that I am pivoting through.
First turn off the mysqld service on the EC2 box:
/opt/bitnami/mysql/scripts/ctl.sh stop
Stop the local mysql server script from restarting on boot:
mv /opt/bitnami/mysql/scripts/ctl.sh /opt/bitnami/mysql/scripts/ctl.sh.disabled
Install rinetd ( this also sets it to start on boot )
apt-get install rinetd
To configure the pivot, add this line to the rinetd configuration file:
localhost 3306 dev-rds.xxxxxxxxxx.us-east-1.rds.amazonaws.com 3306
The configuration file for rinetd is located at /etc/rinetd.conf.
Next, restart the rinetd service: /etc/init.d/rinetd restart
If you want to verify that the server is now listening on port 3306, use netstat:
netstat -ano | grep 3306
After that, you need to configure the client.
Navicat Client
In this instance, I use Navicat to manage the database, and the new connection to the EC2 instance will be via SSH using a public/Private key for authentication.
Configure the General tab of the Navicat connection:
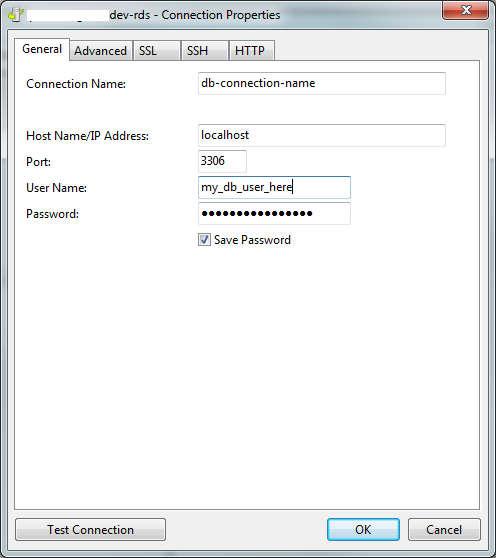 The original host name is now changed to "localhost".
The original host name is now changed to "localhost".
Configure the SSH tab of the Navicat connection:
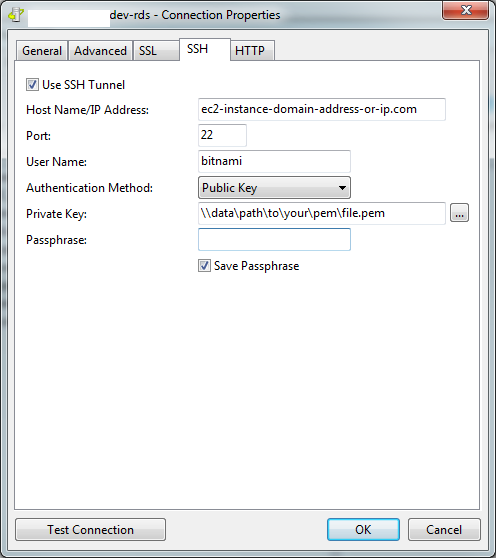 Here, add the host name or ip of the EC2 box, set the path to your pem file, and if you have no password on the pem file, check off the Save Passphrase checkbox.
Here, add the host name or ip of the EC2 box, set the path to your pem file, and if you have no password on the pem file, check off the Save Passphrase checkbox.
That is it, you should now be able to pivot via your Amazon EC2 server to your Amazon RDS MYSQL server and will not have to change the firewall IP's when your IP changes.